CYBER SAFETY CLASS 9 18OCT2023
1 What Is Malware?
Malware or malicious software is the aggregate name of a program which is deliberately designed to cause harm to the computer system, server system, user's computer or computer network. Malware includes viruses, ransomware, spyware, worms, Trojan horses, adware, rogue software, and scareware.
Key symptoms of malware in a computer -
Here are a couple of indications that your computer may be contaminated:
- Computer turns out to be moderate and inert
- computer crashes and restarts much of the time
- Applications on your computer crash much of the time
- Computer's stockpiling is distant or undermined
- Uncommon blunder messages on your computer
- Undesirable popup messages
- Virus
Viruses are intended to harm computer, its objective is to destroy data, reformatting hard drive, or totally closing down computer system. - Worm
One of the most widely recognized kinds of malware, worms spread over computer organizes by misusing working system weaknesses. It's an independent program that imitates itself to contaminate different computers, without requiring action from anybody. - Trojan Horse
Trojan horse, "Trojan", enters computer system masked as an ordinary, disrupt files or program to trick user's into downloading and introducing malware. - Spyware
Spyware can reach into user's computers without their knowledge. Its intended to follow browsing and internet activity. - Ransomware
Ransomware is a kind of malware that can steal and hold users data and than demand money to release back.
Various types of information used by websites to track us online are as follows:
- IP Address — From our IP address, a website can determine our rough geographical location.
- Cookies and Tracking Scripts — They can identify and track our browsing activity across a website.
- HTTP Referrer — When a link to an outside website on a webpage is clicked, then the linked website will get opened and internally our information will be provided to the linked website.
- Super Cookies — Super Cookies are persistent cookies that come back even after we delete them.
- User Agent — It tells websites our browser and operating system, providing another piece of data that can be stored and used to target ads.
3 What is Private browsing ? Why is it considered a better way of browsing the Internet?
Answer
A type of browsing wherein browser opens in incognito mode or through proxy or VPN, and does not store cookies about our online activity, is called Private browsing.
It is considered a better way of browsing the Internet as it allows the user to use the Internet without revealing his/her search history and sharing data.
4 What should you keep in mind while choosing an effective password?
Answer
We should keep the following things in mind while choosing an effective password:
- Use different passwords on different systems and accounts.
- Don't use passwords that are based on personal information that can be easily accessed or guessed.
- Use a combination of capital and lowercase letters, numbers, and special characters.
- Don't use words that can be found in any dictionary of any language.
- Develop mnemonics such as passphrases for remembering complex passwords.
5 What is confidentiality of information ? How do you ensure it ?
Answer
Confidentiality of information ensures that only authorized users get access to sensitive and protected data.
To ensure confidentiality of information, we must follow the following best practices:
- Use firewall wherever possible to ensure only authentic users connect to the computer.
- Control Browser settings to block tracking.
- Browse privately whenever possible to avoid tracking by websites by not storing cookies.
- Be careful while posting on Internet and avoid sharing personal information like address, mobile number, bank details, etc on public Internet sites.
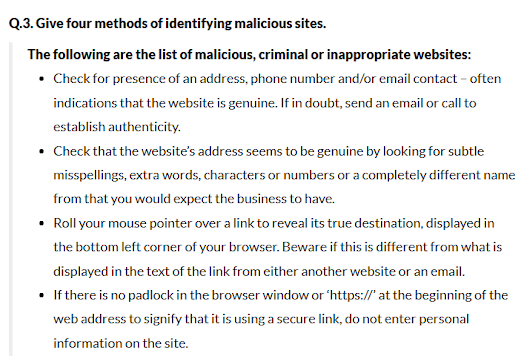
- Ensure safe sites while entering crucial information by checking for https and padlock sign.
- Carefully handle emails by not opening attachments from unknown senders and avoid clicking on links contained in the email.
- Do not give sensitive information on wireless networks.
- Avoid using public computers while dealing with crucial data
Answer
A computer virus is a computer program that can infect other computer programs by modifying them in such a way as to include a copy of itself.
Viruses can alter, corrupt and delete files, freeze the computer, flash unknown or unasked messages or display unwanted graphics on the computer screen, play unwanted music and interfere with the computer operation.
7 What is cyber crime ? How can you report it ?
Answer
Any criminal offence that is facilitated by, or involves the use of, electronic communications or information systems, including any electronic device, computer, or the Internet is referred to as Cyber crime.
A cyber crime can be reported in the following ways:
- The local police stations can be approached for filing complaints with the cyber crime cells specially designated with the jurisdiction to register complaint.
- Provisions have now been made for filing of 'E-FIR' in most of the states.
- The Ministry of Home Affairs is also launching a website for registering crimes against women and children online including cyber crimes.
Answer
Harassing, demeaning, embarrassing, defaming or intimidating someone using modern technologies like Internet, cell phones, instant messengers, social networks etc., is called Cyber Bullying.
Cyber stalking refers to online stalking where someone uses Internet, chat rooms, social networking sites, emails etc. to stalk his/her victim. Cyber stalker follows the victim online everywhere and keeps posting/sending something which are unsolicited.
9 What is the significance of a firewall in a computer's security scheme ?
Answer
A firewall secures the computer such that only authentic users can connect to it. The significance of firewall lies in its ability to monitor, filter, and control incoming and outgoing network traffic based on predefined security rules. This helps prevent unauthorized access, data breaches, and malicious attacks, such as viruses, malware, and hacking attempts, from reaching the protected computer system.
More practice Questions:-


Comments
Post a Comment